During week four I explored Safety To-Dos for Educators such as the
phishing quiz, have you been Pwned, and I did a Google security checkup. It was
very interactive and informative. After doing the phishing quiz I learned
that I wasn’t well versed in all the forms that phishing can take, and I scored
a 4/8. This means there’s a 50% chance that I would have taken the bait and
openly gave cybercriminals access to my information. The quiz allowed me to
learn the difference between a generic greeting and forged links. I must admit,
you have to pay very close attention to your emails to not become a victim of
cyber theft.
An accident happened at my job where a phishing email was sent out to CPL (Chicago Public Library) employees and a lot of staff members weren’t aware that they were being phished and many employees had clicked on the link. Since this happened, we now have to update our passwords every few months. CPL also partnered with Security Mentor to provide security awareness training for all staff members. Some of the lessons we had to take were protecting information, you’re being phished, how secure are your passwords, you are the key to security, and be an email detective. At any rate, several practical steps can be taken to avoid phishing attacks such as, never clinking on a link from an unknown source even if they appear to be from a trusted source, always scrutinize the email address, and be aware of a sense of urgency the messages seek to evoke.
Furthermore, I checked to see if I had been Pwned and it turns out that one of my email accounts had been breached. Then after checking my Google account to do a security checkup, I discovered that I had 13 accounts that my password was compromised on. I immediately deleted the passwords for the accounts that I no longer used and updated passwords on other active accounts. Google also informed me that I had several week passwords and I updated those accounts as well.
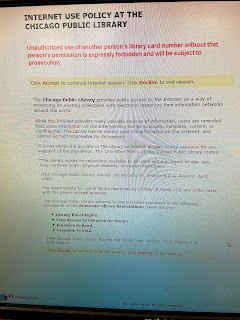
Lastly, The Chicago Public Library’s staff or patrons do not have to sign any policy regarding social media use. However, the patrons who use the Chicago public library’s internet service has to accept the internet use policy before gaining access to the internet. The policy includes an introduction and disclaimer. The policy states that “unauthorized use of another person’s library card number without that person’s permission is expressly forbidden and will be subject to prosecution.” The policy prohibits any use of library equipment to access material that is child pornography.
The policy further states that only computer equipment and software owned and previously installed by the Chicago Public Library may be used on CPL computers, except for patron-owned flash drives, which may be used on all public access computers. Adding, deleting or modifying the installed hardware or software is not permitted. No personal files will be saved on the hard drive. The Library has no control over the information on the Internet and cannot be held responsible for its content. The policy clearly communicates that users are responsible for what they access online, and parents are responsible for their children's Internet use. I think the policy tends to focus more on what patrons shouldn’t do rather than what they should do. I also think there could be some improvement with the policy such as social media guidelines, safe and appropriate computer social behavior, and it could have included more examples of acceptable use.
Computer
and Internet Use Guidelines. (n.d.). Retrieved February 5, 2020, from https://www.chipublib.org/computer-and-internet-use-guidelines/
Harrison, Ashanta. “Internet Use Policy.” 2020. JPEG
file.
I also read an interesting article about phishing. The main takeaway was that communication needs to be open between an institution and its staff. If staff members do not feel comfortable reporting that they have fallen for a phishing scam it can lead to more security breaches in the future. I also decided to conduct a Google security check on my own account for peace of mind. It can be scary to think about how much security is needed to even keep a person's basic information safe.
ReplyDeleteThanks for the reflection. I like the idea of a policy including examples of acceptable use. It not only is positive but lets the patron know if they are being safe using the library's technology.
ReplyDeleteRecently, at the library I work at, we were all given a "phishing test" from administration without knowing it was a test, making it appear that our W2 forms were one click away. I didn't fall for it, but the library director told us that a lot of us did fall for it, so we were required to complete anti-phishing training. I also did not have to sign a social media policy as far as I remember, but we did have to sign for the employee handbook, which included a social media policy in it. There is a decent-sized internet use policy for our patrons as well.
ReplyDeleteThe library I work for also has us change our passwords every few months. It makes it a little difficult to remember them or think of a new password, but it keeps the library and our information safe which I appreciate. We also get notified from the business manager about strange emails that could or are not secure and to watch out for them. Its always good to be aware and take safety precautions when it comes to social media or other accounts.
ReplyDelete